
Permissionless Blockchains Vs Permissioned Blockchains
Written by Sidharth Kumthekar
Reviewed by Logan Ross
J.P. Morgan and BlackRock are leveraging permissioned blockchains to trade while they await regulatory clarity surrounding use of public blockchains such as Bitcoin and Ethereum.
What are Permissionless Blockchains?
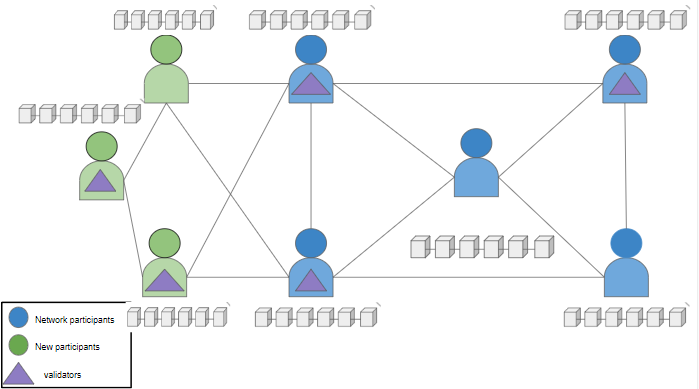
Permissionless blockchains such as Ethereum are borderless, trustless, decentralized public networks that can be accessed, participated in, and validated by anyone. The state of a permissionless blockchain at any given instance of time can be completely reproduced by any user who wishes to validate a past transaction.
Open to all, permissionless blockchains operate without the presence of any administrative control authority. One does not have to complete any KYC (Know Your Customer) procedure in order to access the network.
Features of Permissionless Blockchains
There are four principal features that form the building blocks of any permissionless blockchain network.
1. Transparency
Permissionless blockchains are proven to be highly decentralized and transparent. Every transaction and data recorded on a permissionless blockchain is publicly accessible and verifiable.
Indexing tools like blockchain explorers can be used to extract details of every recorded transaction using addresses, transaction IDs, or block numbers.
2. Anonymity
Permissionless blockchains like Ethereum, Bitcoin and Solana are pseudo-anonymous. Users can preserve their true identity by representing themselves through a cryptographically derived public address, which corresponds to the public keys that are derived from the private keys, safeguarded by the users.
Hence, users do not need to provide any personal information like username, email, or password to access and participate in the network.
3. Censorship Resistance
Permissionless blockchains are designed to be censorship-resistant. As the power to control the network does not vest in the hands of a single entity, the risk of censoring an address or a transaction is relatively low.
4. Consensus
The strength of a permissionless blockchain lies in its consensus mechanism. Anyone can participate in the consensus by either staking the minimum required number of coins (for PoS chains) or by maintaining validator nodes (for PoW chains). As the number of validators increases the risks of partial centralization and 51% attack decreases.
Native cryptocurrency is an important element in the open consensus model of permissionless blockchain which incentivizes miners and stakers for their effort to maintain the consensus and validate transactions.
Advantages of Permissionless Blockchains:
Compounding its core features, permissionless blockchains provide the following benefits.
1. Liquidity
Permissionless blockchains are open to anyone who wishes to join and participate making them the ideal place for global liquidity to pool.
2. Continuous Innovation
The majority of the permissionless blockchains are open-source, i.e. the network's infrastructure code is publicly accessible. This enables developers around the world to contribute to the network by proposing improvements to the network's infrastructure, initiating forks, and developing Decentralized Applications (DApps) to improve overall onchain user experience and network security.
Disadvantages of Permissionless Blockchains
Some of the principal Layer 1 blockchains like Ethereum and Bitcoin suffer from the following inherent challenges.
1. Scalability
The throughput of a network is dependent on:
the type of consensus mechanism used
block time (time taken to mine a block)
the size of the network, and network fees (gas fees)
As the network expands, the time required to reach consensus increases which may cause congestion during periods of higher traffic, resulting in delayed transaction confirmation and a surge in network fees.
2. Dark Forest
Anonymity in permissionless blockchains opens the door for malicious actors to enter the network without getting detected. Profiteering actors on the public network find ways to take advantage of those who accidentally leave money on the table, or do not properly secure their transactions.
Alternatively, attacks can be directed towards decentralized applications built on top of programmable blockchains like Ethereum. Hackers can exploit vulnerabilities in the deployed smart contract to drain its funds or even worse, gain complete control over the contract.
Permissionless Blockchain Use Cases
Openness in public-permissionless blockchains opens the door to a plethora of unique use cases and applications. Some of the noticeable and widely adopted use cases are.
1. Decentralized Finance
DeFi transactions contribute towards the majority of onchain activity on permissionless blockchains. They involve the use of publicly tradable cryptocurrencies which can be utilized for lending, borrowing, yield-farming, and staking on various Defi platforms like swaps, exchanges, bridges, and more.
2. Digital Asset Tokenization
Permissionless blockchains have attracted digital artists and creators to utilize the underlying tokenization infrastructure for various creative applications like NFTs and Gaming with onchain benefits like:
Immutability
ownership verification
transparency in royalty distribution
3. Dapps and DAOs
Programmable public blockchains like Ethereum provide developers the ability and the freedom to develop decentralized applications and onchain publicly governed organizations (DAOs) for use cases like donations, crowdfunding, communication, video streaming, storage, asset tracking management, and more.
What are Permissioned Blockchains?
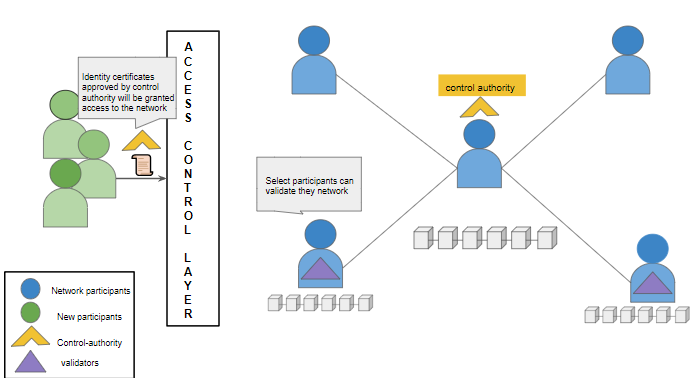
Permissioned Blockchains are private chains made for specific enterprises or ecosystems. In these networks, a central authority or organization specifies the rules to regulate the network.
Permissioned blockchains have a strict access control layer that permits only approved members to participate. Network information and data are kept private from the public.
Primarily used in enterprise use cases like banking, supply-chain management, B2B interaction, government applications, identity management, and more.
Permissioned blockchains are hierarchical in nature where privileged entities have higher rights to access sensitive network information.
Features of Permissioned Blockchains
The key features that principally differentiate permissioned blockchains from permissionless networks are:
1. Privacy
Transparency is optional in permissioned blockchains. Depending upon the use case, transaction records can be chosen to be kept private/hidden from other participating organizations in the network.
For instance, organizations may not want their interactions with petroleum distributors to be visible to their competitors. Therefore, they can opt to record these dealings privately rather than publicly.
2. Anonymity
The degree of anonymity in permissioned blockchains varies up to the network administrator/s who holds the authority to regulate the access privileges granted to each user.
Preserving the anonymity of participants is not an essential prerequisite in Permissioned Blockchains.
In the case of a hierarchical setup, the entity at the apex retains the ability to identify and authorize every participant of the network.
For example:
Consider a supply chain management framework built on a Hyperledger Fabric network. In this hierarchical setup, the regulatory body can have the authority to identify the personal details of every participant in the network.
3. Censorship
While designing a permissioned blockchain, authorities and stakeholder organizations can establish specific regulations tailored to their business needs.
Regulations enable the authorities to govern and control the state of the network which may lead to censoring certain users from participating in the network or placing limitations on specific transaction types that do not align with the network's rules.
4. Consensus
Since Permissioned blockchains are confined to an enterprise model, they do not need to operate on the consensus mechanism used by public permissionless blockchains. Instead, the centralized operator can establish its own consensus using public or proprietary methods.
Two of the most common private blockchain consensus mechanisms are Practical Byzantine Fault Tolerance and Federated Byzantine Agreement:
Practical Byzantine Fault Tolerance (PBFT):
The PBFT algorithm enables a distributed system to reach consensus even if there are fewer malicious nodes present in the network. The algorithm states that, in a network of 3f+1 nodes, consensus can be achieved as long as a minimum of 2f+1 non-malicious nodes are operating properly where f is equal to the number of byzantine nodes.
Federated Byzantine Agreement (FBA):
The FBA mechanism is based upon the principles of BFT which ensures that the network can achieve consensus even in the presence of malicious or faulty nodes. The algorithm uses the concept Quorum and Quorum slices which allows nodes in the network to form a group of trusted peers called Quorum slice. A Quorum represents the minimum number of mutually trusted nodes required to reach a consensus.
Advantages of Permissioned Blockchains
Due to their restrictive nature, permissioned blockchains share the following benefits.
1. Modular Consensus
Modular consensus provides the flexibility to switch between multiple consensus algorithms without needing to modify the underlying infrastructure and protocol layer of permissioned blockchains. Some of the permissioned Blockchain projects that support the modular models are Hyperledger, Corda, and Hedera.
2. Privacy
Permissioned blockchains maintain a strict access control layer which is responsible for admitting entry to those entities only that have the access certificate (issued by the control authority). This ensures that no outsider can access and interact with a permissioned blockchain without being authorized by the control authority.
3. Scalability and Performance
Permissioned blockchains are typically more performant than traditional permissionless chains like Ethereum and Bitcoin. The reason is being, the number of validator nodes in a permissioned network is limited in number and is already pre-decided by the network administrator. Hence, time to confirmation and finality is much faster and deterministic.
4. General Purpose Programming Language Support:
Many Permissioned blockchain frameworks support general-purpose languages like Go, Java, and Javascript to develop smart contracts. e.g. Hyperledger provides multi-language support for developing smart contracts which include Java, Go, and Node.js. Even Corda allows you to develop applications using Java.
Disadvantages of Permissioned Blockchains
The ability to administer the network in permissioned blockchains is exercised by only a few privileged entities, thereby introducing the following drawbacks.
1. Centralization
Permissioned blockchains may have entirely centralized control over the chain, which may be a pro or a con depending on your use case. Typically, centralized chains will be used for internal operations where decentralization is not desired or necessary. In this case, centralization is not a disadvantage.
2. Lack of Transparency
Not every participant in a permissioned blockchain has the authority to validate the correctness of transactions.
Instead, only a select group of validators appointed by the control authority wield the power to do so, which may lead to censoring targeted transactions or manipulating the network for personal benefit. For internal operations, this is not a disadvantage.
Permissioned Blockchain Use Cases
The most widely used Permissioned Blockchain use cases are:
1. Digital Asset Settlement
JPMorgan and BlackRock’s foray into tokenized collateral settlements on the permissioned Tokenized Collateral Network (TCN) indicates a shift towards a more composable solution for physical asset management within corporations.
JPMorgan Onyx’s initiative to tokenize collateral infuses traditional assets with greater composability within their permissioned ecosystem and unlocks new pools of liquidity.
2. CBDCs
Central Bank Digital Currency is a digital alternative to any traditional country-specific fiat currency, regulated by the Central Banks of respective countries. A CBDC network can be built using Permissioned blockchains with primarily three participants - the Central Bank, Commercial banks, and end-users.
3. Health and Pharmaceutical
Permissoned Blockchains can be used to keep track of patient history privately and share it securely with other member hospitals of the network. In pharmaceutical industries, permissioned blockchains can be used to record the distribution status of drugs right from production to the market, to avoid counterfeit drugs from entering the market.
4. Supply Chain Management
Creating onchain solutions to enable transparent end-to-end tracking of goods while maintaining private records of transactions between member organizations.
How to Get Started Building
Whether you are going to be building on public or private chains, it’s important to familiarize yourself with the enterprise blockchain tech stack.
How to Start Building on Permissionless Blockchains
Here’s a step-by-step breakdown of how you can rapidly start building on Permissionless Blockchains with Alchemy.
1. Choose the right chain to build on
Permissionless blockchains offer a wide variety of technologies and chains to develop upon. Developers can choose between various chains, and select the right tech stack that best suits their application needs.
2. Choose between a Layer 2 solution
Additionally, developers can choose to scale their DApp by developing applications on top of Layer 2 protocols using specialized SDKs provided by these Layer 2 solutions. Example: EVM-compatible Layer 2 Optimistic Rollups like Arbitrum and Optimism. Sidechains like Polygon.
3. Create an Application on Application
Create the Application for free by using the respective Alchemy RPC node URL for the selected chain.
4. Acquire test tokens
To deploy the DApp, developers need to get access to respective test network tokens from the Alchemy faucet Once, the app is battle-tested the production version can then be deployed to the main network.
5. Write, Compile, and Deploy the smart contract
To get started with writing smart contracts Visit Alchemy Docs to build a simple “Hello world “ smart contract.
6. Interact with the smart contract and integrate it with the front end
Once developing the smart contract, one needs to know how to interact with it. Follow the guide for a step-by-step walkthrough. Follow this guide to integrate the smart contract backend with the front-end client interface.
How to Start Building on a Permissioned Blockchain
To start building application-specific permissioned blockchains the very first step is to define the scope of the application and which use case it is based on.
1. Hyperledger
Hyperledger is one of the earliest open-source enterprise blockchain platforms established by the Linux Foundation in 2015. Hyperledger constitutes a fleet of 13 unique open-source Distributed Ledger Technology (DLT) frameworks, each having its own specialty and use case.
HyperLedger Aireis - For building applications for digital identity management
Hyperledger Besu - Used for developing hybrid (both public and private) enterprise solutions in the Ethereum ecosystem
Hyperledger Fabric - The most widely used enterprise-grade modular blockchain framework
Hyperledger Besu Stack
Hyperledger Besu - Java-based OSS Ethereum Client co-maintained by Consensys
Orion - Private transaction manager for HyperledgerBesu
EthSigner - Client Agnostic Ethereum Cient Signer based in Java
2. Corda
R3’s Corda is an open-source DLT application development platform built indigenously using Java APIs. Used to develop application-specific interoperable blockchains.
3. Consensys Quorum
Quorum is an open-source protocol layer used to build enterprise solutions leveraging Enterprise Ethereum.
Quorum consists of two stacks: Hyperledger Besu Stack and the Consensys GoQuorum Stack.
Consensys GoQuorum Stack
Go Quorum - Open-source Ethereum client written in GoLang and maintained by Consensys
Tessera - Private transaction manager for GoQuorum
EthSigner - Client Agnostic Ethereum Cient Signer based in Java
After selecting the right platform to build on, the project development can be initiated by installing the required tools, libraries, and dependencies.

Related overviews
Everything You Need to Know About RPC Nodes for Building Onchain
What Are Private RPC Nodes and Endpoints? How to Create a Private RPC Endpoint in 2025.
Explore the Best Blockchain Node Infrastructure Providers for Building Onchain.
