
What Are Cross-Chain Bridges?
Written by Alchemy
There are hundreds of blockchains with onchain activity today, each with their own approach to scalability, security, decentralization, and a host of different traits. One thing that all of these blockchains have in common? Users want to be able to move assets and data between them. That’s where cross-chain bridges come in.
Over the last few years, bridges have evolved from simple “wrapped‑asset ferries” into programmable pipes that move tokens and arbitrary messages between all of these blockchain networks. The total value locked (TVL) in bridges now reaches $55B, which speaks to both the market demand for them and also the risk—bridge exploits still dominate crypto‑hack leaderboards.
Whether you’re a hands‑on engineer integrating bridge SDKs or a GTM leader sizing new markets, this guide will give you all of the context you need on the state of cross-chain bridges in 2025.
What Is a Cross‑Chain Bridge?
A cross-chain bridge connects independent blockchains together and enables the transfer of assets and information between them, allowing users to access other protocols easily. You can think of a cross-chain bridge as middleware that lets state move between networks that were not designed to talk to each other.
That same type of middleware exists with global banking rails: your credit card can work at both a New York bodega and a Tokyo konbini because payment networks can translate between issuers and banking providers. Bridges do the same for blockchains.
Bridge Tranfers vs. CEX Transfers
Before blockchain bridges enabled users to easily move assets between blockchain networks, the only way to migrate assets from chain A to chain B was to:
Send tokens from Chain A to a centralized exchange (CEX).
Trade those tokens for different tokens compatible with Chain B.
Withdraw those new tokens to Chain B.
Bridges collapse those three steps into 1 on‑chain transaction, slashing fees and keeping users self‑custodial.
How Does a Cross‑Chain Bridge Work?
The Classic Lock‑and‑Mint Model
Most first‑generation bridges wrapped assets using a lock‑and‑mint pipeline, using a custodial solution where a 3rd party facilitates the bridging to another chain via the following steps:
Deposit: Alice sends 10 ETH to the bridge contract on Ethereum (the source chain).
Lock: A validator set or custodian locks the ETH in a vault.
Mint: The bridge mints 10 wETH on Polygon (destination chain) and releases it to Alice’s wallet.
Redeem: When Alice is finished transacting on Polygon, she burns the 10 wETH on Polygon by sending the wETH to a particular address.
Unlock: Validators trigger the release of the original 10 ETH back to Alice on Ethereum.
One key detail to remember with this bridge design is that the ETH never leaves Ethereum. Users trade their custody on Chain A for a claim for those assets on Chain B. That custody layer—who controls the vault on Chain A—defines much of a bridge’s risk profile.
This is an important point, so let’s make that more explicit. You can’t actually send assets from one chain directly to another, e.g. you can’t send BTC to an address on the Ethereum network. Instead, you have to lock BTC on the Bitcoin chain and mint a new asset on the destination chain.
This is sometimes called “wrapping” a token (hence the name wrapped Bitcoin or wrapped Ethereum) as a way to describe the bridging process, where the asset is “wrapped” in a smart contract in order to make it programmable and functional on the destination chain B.
Beyond Wrapping: Native Burns & General Message Passing
Over time, bridge design has gotten more sophisticated, so the most basic version of lock and mint (which introduces custodial risk) has evolved into new designs and capabilities, such as:
Burn → Mint: Rather than lock up tokens on chain A to mint them on chain B, some bridges now enable users to destroy the token on chain A (”burn” it) and then mint a new token on chain B. For example, this is how Circle’s CCTP works, where users can burn USDC on chain A to mint native USDC on chain B.
General Message Passing (GMP): Enabling assets to move between blockchain networks was the first implementation of a bridge, and now bridges also facilitate the passing of arbitrary messages (aka data), unlocking crosschain use cases, where smart contracts on one chain can react to state on another chain (e.g. you could pay a loan on Optimism when collateral on Arbitrum is liquidated). Bridges like Chainlink CCIP and Axelar GMP facilitate this kind of cross-chain data transfer.
Why Cross‑Chain Bridges Matter in 2025
Cross‑chain infrastructure is no longer a “nice‑to‑have.” It has become the connective tissue of the crypto economy—quietly stitching together dozens of otherwise siloed networks and unlocking use‑cases that were impossible just a year or two ago.
At a high level, bridges offer the following value to users:
1. Liquidity routing: Deeper liquidity means better price discovery and less price fluctuation during large trades. It’s a better user experience, and bridges can aggregate liquidity across different chains, enabling better pricing and better price discovery.
2. Asset productivity: Many users “hodl” assets and sit on them. Bridges allow users to move assets between blockchain networks and put those assets to work in different apps. Maybe you want to lend BTC on OP mainnet, or maybe you want to use an Ethereum NFT as collateral on Solana. Bridges are what makes that happen.
And for apps, bridges can help streamline operations and abstract away complexity:
3. Cross-chain account abstraction: Smart wallet infrastructure such as Alchemy’s Smart Wallets let users sign one transaction on the front end, while the backend quietly settles across multiple chains and handles bridging behind the scenes. That abstraction slashes onboarding friction, vital for consumer apps that don’t want to explain chains at all to their users.
4. Enterprise settlement & stablecoin payments: Corporations like PayPal rely on Chainlink CCIP to send PYUSD to merchants who may prefer to settle on Polygon or Base instead of Ethereum. A single, chain‑agnostic payout rail keeps compliance and treasury logic simple while still meeting users where they are.
Taken together, these pillars signal a shift from a multi‑chain world—where users consciously hop between chains—to a chain‑abstracted future where the bridge plumbing is invisible and instantaneous.
Security and Risk
With so much value locked in bridges ($55B!), bridges have become honeypots for hackers. To date, more than $2.8B has been hacked from cross-chain bridges, and looking at the Rekt leaderboard you’ll find many bridges. The lessons learned generally fall into 2 types of exploits:
Key compromise: custodial or multisig bridges collapse if attackers capture a signing quorum, as seen in the infamous $620M Ronin hack.
Logic bugs: even “trust‑minimized” bridges can mishandle proofs. Wormhole lost $320 million when a single missing verification check let an attacker mint wrapped ETH out of thin air.
Alongside the bug exploits described above, you also have risk in bridge liveness (where the bridge could stop working if operators cease functioning) or theft (bridge operators behave maliciously and take funds).
Over time, bridges have gotten more secure and battle-tested, but even now bridge exploits are still a risk. If you’re assessing whether a bridge is safe to use or not, keep an eye out for the following signals:
Has the bridge been operational and secure over a long period of time without hacks?
Have the bridge contracts had at least 2 independent audits?
Does the bridge have an active bug bounty? If so, how much?
Do validators and relayers have a slashable stake if they behave dishonestly?
Does the bridge offer a time-locked upgrade path, so users can react to code changes?
Thinking through these questions won’t guarantee safety, but it can help you identify red flags in poor bridge design.
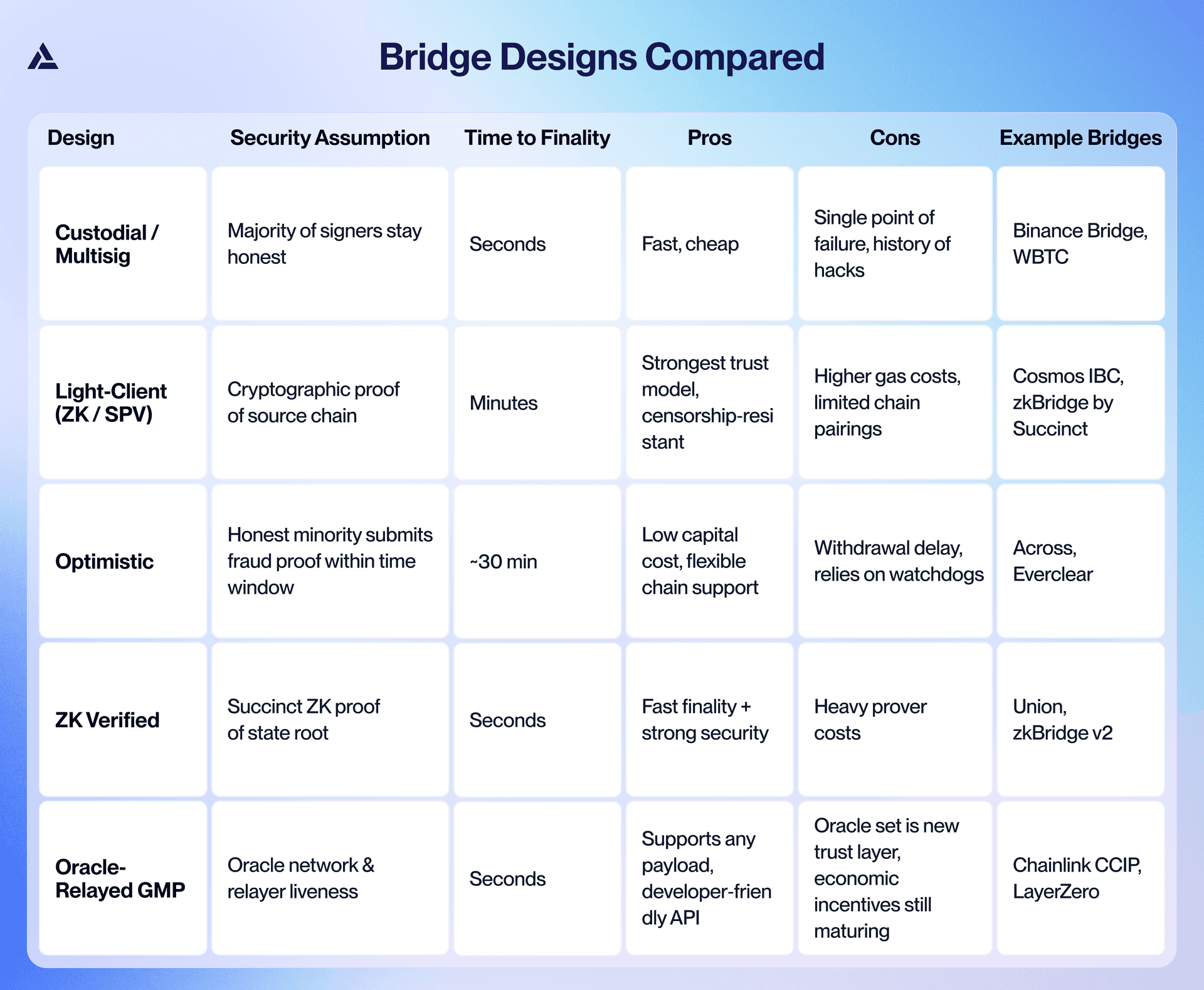
Bridge Designs Compared
Over the last few years, bridge design has evolved to meet a number of different use cases and user preferences. At a high level, these are the categories available on the market today:
Which Bridge Design Should You Use?
There’s no right or wrong answer here, and which bridge you use might depend on your needs and how comfortable you are trusting a 3rd party bridge operator. For small transfers, trusting a bridge operator may not be a big deal, and you may want to optimize for fast deposite times and good UX, but at larger sizes, you may want a trustless solution and are comfortable with longer confirmation times.
One other piece of the puzzle is that different bridge providers support different bridge networks. You not only need to consider the design tradeoffs of the bridge you use, but which chains it supports as well.
The 2025 Bridge Landscape
There are a wide number of general ecosystem bridges that help you connect to those respective ecosystems (e.g. Binance bridge, Polygon bridge, and the Avalanche bridge). Alongside those ecosystem-specific bridges, there are a number of 3rd-party providers that specialize in this bridging function, and the market has consolidated around a handful of heavyweight protocols—each staking out a different spot on the security‑speed trade‑off curve.
The upside of all of these options: developers no longer need to place one big bet on a single bridge. Instead, aggregators increasingly stitch these protocols together, routing each transfer through the cheapest secure path in real time.
Here are some of the major players in the space today:
Allbridge
Allbridge is a multichain bridge spanning EVM and non-EVM chains (including Ethereum, Ethereum L2s, Solana, Tron, and Sui). As of August 2025, Allbridge Core shows roughly $23M in TVL. This bridge provider focuses on straightforward stablecoin swaps between different ecosystems and also offers liquidity pools and yield opportunities for users.
Across
Across is an “optimistic” bridge secured by UMA’s Optimistic Oracle with bonded relayers and single-sided LP pools, purpose-built for fast settlement. Its prioritization of speed has led Across to a current TVL of $98M and $1.3B in volume over the last 30 days, and the protocol supports 20 different blockchain networks.
Axelar
Axelar is a general message passing (GMP) network that connects EVM chains, Cosmos IBC zones, and more, enabling both token transfers and cross-chain calls. With $320M in TVL, Axelar’s appeal is developer ergonomics and broad ecosystem reach; the tradeoff is its additional protocol complexity.
Celer cBridge
cBridge is a non-custodial liquidity bridge built on Celer’s inter-chain messaging, with fast transfers and an SDK developers like. cBridge has $67M in TVL and supports 40+ blockchains. Design-wise it leans on liquidity networks for speed (vs. pure lock/mint), trading some path dependence and routing complexity for UX.
Chainlink CCIP
Chainlink CCIP offers enterprise-grade cross-chain messaging and token transfer across ecosystems supported by Chainlink’s oracle service, which currently secures $59B onchain. Its secret sauce is a pooled Oracle‑plus‑validator model and the new Cross‑Chain Token (CCT) standard, which lets enterprises launch assets that feel native everywhere. The bridge introduces opinionated security layers like the “Risk Management Network” that blesses messages off chain, which in turn creates more operational limits compared to other options.
deBridge
deBridge uses a “0-TVL” design that operates like an order book (makers fill cross-chain orders across the liquidity network) rather than a pooled bridge, which minimizes idle capital and wrapped-asset risk. You can see that design play out in its traction: deBridge only has $12M in TVL, but has processed $793M in volume over the last 30 days. In exchange for the tradeoff, the network relies on off-chain market makers and order matching.
Everclear (Connext)
Everclear is a bit different than other entries on this list: it’s not a traditional bridge that’s end-user facing. Instead, it’s a clearing layer that nets cross-chain flows, so bridgers rebalance less, cutting down their costs. Rebranded from Connext in 2024, Everclear’s beta reports fees as low as 2bps, and the network is pushing towards a full mainnet launch in 2025.
IBC
IBC is Cosmos’ trust-minimized, light-client-based protocol (with no middlemen). This bridge connects 115+ chains and facilitates $700M in monthly volume. This bridge’s security model is excellent when both chains run robust light clients; the tradeoff is that integrating this bridge beyond the Cosmos SDK stack requires additional engineering (though IBC v2 hopes to fix this).
Portal (Wormhole)
Portal is one of the most popular bridges on the market and leverages Wormhole’s general-message network. With nearly $3B in TVL and processing $1.1B in volume every month, Portal offers chain coverage and a mature messaging layer, but it does rely on a validator/guardian model and has a notable hack in its history.
Stargate (LayerZero)
Stargate offers a bridge built on LayerZero’s DVN security stack and supports 40+ chains. With deep integrations across major L1s, Stargate has $370M in TVL. If you need native-asset routes and single-pool UX, Stargate is the canonical example.
Building with Bridges on Alchemy
Bringing cross‑chain UX into your product used to mean running multiple RPC nodes, writing brittle scanner scripts, and maintaining custom indexers. Alchemy abstracts that complexity away:
Unified multi‑chain RPCs: a single API key unlocks reliable endpoints for 50+ different blockchain ecosystems. No need to juggle infrastructure vendors as you expand.
Webhook notifications: subscribe to events like
DepositInitiatedorMessageExecutedacross bridges. Your backend gets a push notification the moment funds are locked on one chain or minted on another—perfect for updating UI state without parsing entire blocks yourself.
Combine those primitives with an aggregator SDK such as LI.FI or Socket, and you can launch a production‑grade, chain‑abstracted onboarding flow in an afternoon.
Key Takeaways and Next Steps
Cross‑chain bridges have evolved from experimental wrappers to mission‑critical infrastructure. The builders who master this layer today will be best positioned for tomorrow’s chain‑abstracted user experiences.
If you’re ready to explore building onchain, spin up a free Alchemy account, make your first API call, and start building.
Frequently Asked Questions
What is a cross-chain bridge?
A cross-chain bridge connects independent blockchains and enables the transfer of assets and information between them, acting as middleware that lets state move between networks not designed to talk to each other.
How does a cross-chain bridge work?
Most bridges use a lock-and-mint model where tokens are locked on the source chain and equivalent amounts are minted on the destination chain. The original assets never actually leave the source blockchain—users trade custody on Chain A for a claim on those assets on Chain B.
What problems do cross-chain bridges solve?
Bridges enable liquidity routing across chains for better pricing, allow users to put idle assets to work in different apps, and support cross-chain account abstraction that simplifies user experiences by handling bridging behind the scenes.
Is a bridge aggregator the same thing as a bridge?
Not quite. A bridge moves value or messages between two specific chains. An aggregator sits one layer higher and decides which bridge to use for each hop, factoring in cost, liquidity, and security preferences.
Why do exit times vary even within the same bridge?
Latency is a function of both the bridge’s security model and real‑time network congestion. An optimistic proof window might be 30 minutes on paper, but block times and gas spikes can stretch that to an hour in practice.
Can I insure against bridge failures?
Yes—cover providers like Nexus Mutual and Unslashed now offer dedicated policies for leading bridges, typically priced between 2 % and 6 % of the insured amount per year.
What are the main security risks of using bridges?
Bridge exploits have resulted in over $2.8B in losses, primarily from key compromise (attackers capturing signing control) and logic bugs in smart contracts that can allow unauthorized minting or withdrawals.
What's the difference between trusted and trustless bridges?
Trusted bridges rely on centralized parties or small validator sets to hold assets and verify transactions, while trustless bridges use on-chain verification, distributed validators, and cryptographic proofs to minimize reliance on intermediaries.
Can bridges transfer more than just tokens?
Yes, modern bridges support General Message Passing (GMP), enabling arbitrary data transfer and allowing smart contracts on different chains to communicate and trigger cross-chain actions.
What should I look for when choosing a safe bridge?
Look for bridges with long operational histories without hacks, multiple independent audits, active bug bounties, slashable validator stakes for dishonest behavior, and time-locked upgrade paths that let users react to code changes.
Do I need to use multiple different bridges?
Not necessarily—bridge aggregators now route transfers through the cheapest secure path in real-time, allowing you to access multiple bridge protocols through a single interface rather than choosing just one provider.

Related overviews
Looking for the best Hyperliquid RPC in 2026? This guide showcases the best providers.
Learn about the role of indexers and how they help you query onchain data.
Understand the differences between permissioned and permissionless chains and how to choose the right one.

Build blockchain magic
Alchemy combines the most powerful web3 developer products and tools with resources, community and legendary support.